

Have you heard of Pegasus? is a type of email scam that targets people worldwide, threatening to release compromising information. To prevent this, the email message asks to pay the ransom to a Bitcoin wallet. All the claims in the message are complete and utter lies, and all the scam holds exclusively on social engineering.
Email scams have become an increasingly popular attack on individuals, bearing on users’ unawareness about how malware works. “Have you heard of Pegasus” does exactly this: scares the user with the name of a well-known spyware, making them believe the threats are real. In this post, I will explain every single element of this scam, so next time you will recognize it immediately.
Have you heard of Pegasus? scam is a common name for email messages that contain text with claims of possessing compromising photos and videos of the user. The text of the message may differ, but it always contains mentions of Pegasus spyware. One of the latest text variants (as of early June 2024) is the following:
Click to expand the scam email text Hello pervert,I want to inform you about a very bad situation for you. However, you can benefit from it, if you will act wisely.
Have you heard of Pegasus? This is a spyware program that installs on computers and smartphones and allows hackers to monitor the activity of device owners. It provides access to your webcam, messengers, emails, call records, etc. It works well on Android, iOS, and Windows. I guess, you already figured out where I’m getting at.
It’s been a few months since I installed it on all your devices because you were not quite choosy about what links to click on the internet. During this period, I’ve learned about all aspects of your private life, but one is of special significance to me.
I’ve recorded many videos of you jerking off to highly controversial porn videos. Given that the “questionable” genre is almost always the same, I can conclude that you have sick perversion.
I doubt you’d want your friends, family and co-workers to know about it. However, I can do it in a few clicks.
Every number in your contact book will suddenly receive these videos – on WhatsApp, on Telegram, on Skype, on email – everywhere. It is going to be a tsunami that will sweep away everything in its path, and first of all, your former life.
Don’t think of yourself as an innocent victim. No one knows where your perversion might lead in the future, so consider this a kind of deserved punishment to stop you.
Better late than never.
I’m some kind of God who sees everything. However, don’t panic. As we know, God is merciful and forgiving, and so do I. But my mercy is not free.
Transfer $1220 USD to my Bitcoin wallet: 1JVMTup4zuS1JMGXAYYRgvyr2PUmNnY6g2
Once I receive confirmation of the transaction, I will permanently delete all videos compromising you, uninstall Pegasus from all of your devices, and disappear from your life. You can be sure – my benefit is only money. Otherwise, I wouldn’t be writing to you, but destroy your life without a word in a second.
I’ll be notified when you open my email, and from that moment you have exactly 48 hours to send the money. If cryptocurrencies are unchartered waters for you, don’t worry, it’s very simple. Just google “crypto exchange” and then it will be no harder than buying some useless stuff on Amazon.
I strongly warn you against the following:
) Do not reply to this email. I sent it from a temp email so I am untraceable.
) Do not contact the police. I have access to all your devices, and as soon as I find out you ran to the cops, videos will be published.
) Don’t try to reset or destroy your devices.
As I mentioned above: I’m monitoring all your activity, so you either agree to my terms or the videos are published.
Also, don’t forget that cryptocurrencies are anonymous, so it’s impossible to identify me using the provided address.
Good luck, my perverted friend. I hope this is the last time we hear from each other.
And some friendly advice: from now on, don’t be so careless about your online security.”
The text goes under a rather strict pattern: beginning, where the scammer introduces himself as a pro hacker. They claim to have explicit photos or videos of you watching adult content, and threaten to publish it to all of the contacts you have in your phone book. Having such comprehensive access is explained by installing Pegasus spyware into all the user devices.
In certain cases, the author adds a password or two that you could really have used in the past. This, although is a pure manipulation, makes the email much more convincing. After that, the fraudster switches to the main course of the scam: demand to send money (usually around $1000-$1500) to a specified BTC address.
1JVMTup4zuS1JMGXAYYRgvyr2PUmNnY6g2
12PY3MibuWtNHjszG4YMSaSEFf6Y8P2zcN
1AXNYLDEG5YEzc2eyUh7SUYYKeRUaRwseu
17KHqeibF7TWfb9dvPRrbRhvwpkYPd8R3R
ltc1q2yd2s2nq8vgw3swqfhudztarrfwakj96tk7s82
ltc1qughecqtek6x5mfjrhwf0wvg8cqgdehmhyxkluw
ltc1qpj5nfh4j6p7fnn5zwt8jsukz6fum2uj4use6e5
1Dz3tE5mspT4fk9fxkfZk6fBcgav28XxRd
ltc1qjpua6w4zqvhdwlt7hdesshu9fgjfl0525lxvew
1P1muuaa35mkDDxaKZcvTSUqPAtMo1j8nr
ltc1qpyvf4vkw8xg775jduf4uwyecesgd93g579skm7
bc1q34vjur6yxxra3mjktr2qu5wrkvelgrw47wf93k
ltc1q33rqzm8ry5q3y7nv7m8degk9smp6aqxd0lt9z4
As I’ve mentioned at the beginning, all the claims are lies and manipulation, called to scare the user and make them believe the attack is real. This fear, in turn, makes the victim obedient and forces to follow the guidance to pay the ransom. However, a closer look at pretty much every element, especially for a tech-savvy user, reveals that the message is full of questionable claims. Let’s get through this scam, top to bottom, to see what exactly is wrong.
We begin with the introduction, where the alleged hacker calls the victim a pervert and claims “a very bad situation” for the victim. Then they immediately claim using Pegasus spyware on all the victim’s devices, saying that “It works well on Android, iOS, and Windows”. And that is where the first issue comes into view.
Pegasus is a real spyware, a military-grade one, developed by Israeli-based NSO Group. It is a really powerful tool, but the thing is – it works only on iOS and Android, and has stability issues with the latter. Windows was never in scope of this malware, and was in fact never targeted by NSO products.
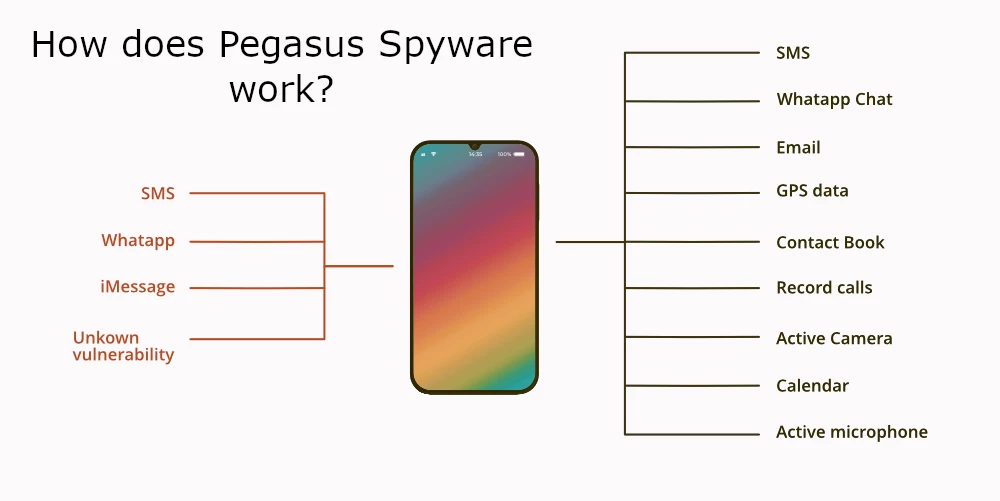
One more thing is that Pegasus is not for sale to everyone. The developer markets its solution only to governments, and only after quite long haggling regarding areas of use. There were – and are – quite a few offers of Pegasus for sale on the Darknet, but every single one of them to date appears to be a fake.
Email body continues with the claim about spying on the victim for a few months, and all the infection was happening through shady links on the Internet. That is just a double load of nonsense. Spying on a specific person for quite some time – well, people know this as stalking, but no one does this on an industrial scale. Considering the number of these emails, they should be attacking thousands of people, but earning money in the way they do is simply counterproductive. By selling just the credentials, without having to collect explicit graphic materials for months, they could get more money and much faster.
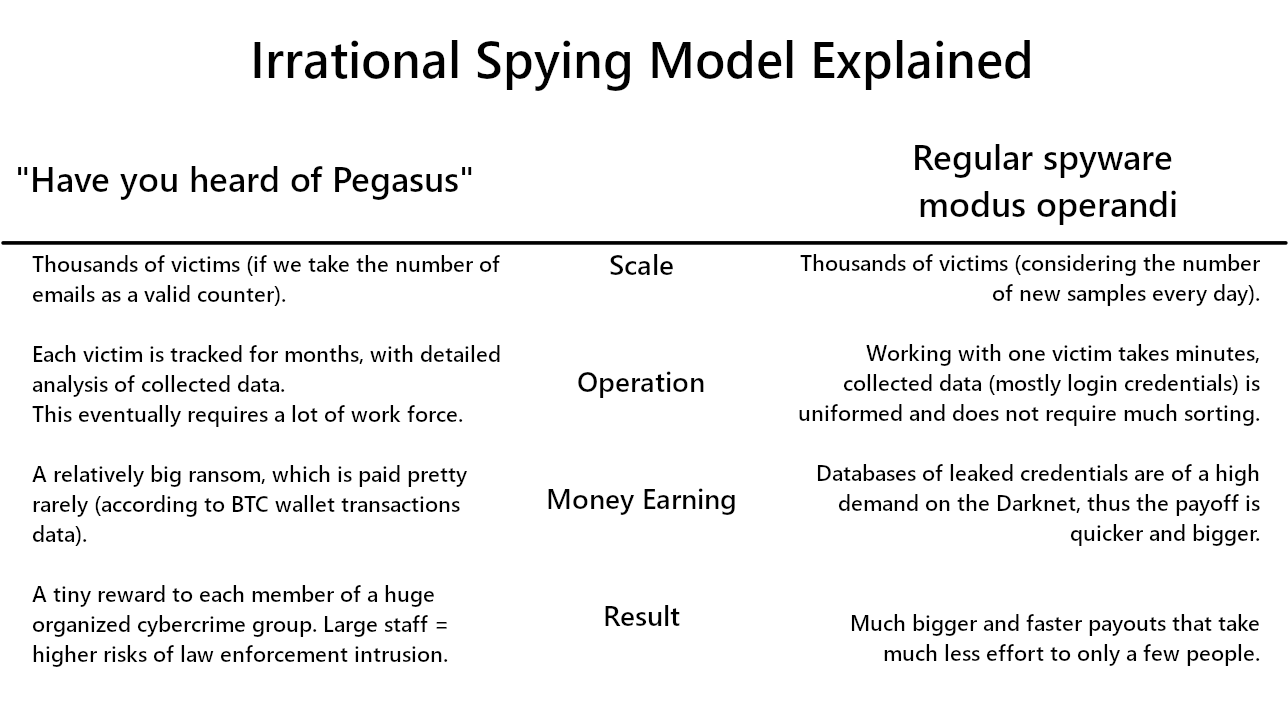
Aside from the time-wasting strategy, the infection vector is also really strange. By the “links on the Internet” the hacker most likely meant deploying malware through exploiting web browser vulnerabilities. And while it is a real thing, it is once again counterproductive to infect single users in such a tricky way. Creating an exploit code usually supposes targeting it on a specific victim (or a small group), and is time- or money-consuming regardless. Once again, the number of “victims” they mail means wasting too much time and effort into creating the exploits. And considering that the majority of web browsers these days have auto-updates, it is hard to find a victim with an unpatched vulnerability.
Overall, both elements seem unreasonably complicated, and are just not how malware attacks usually work.
The message further takes us to the part where the hacker claims possessing the recordings of the victim in some truly embarrassing circumstances, specifically while watching adult videos. What’s worse, at least if we believe in what the letter says, the genre of the said adult videos is compromising and says about the victim’s perversion on the topic. And here is a sign of a scam: there is not even a single mention of anything specific. Threat actors write the text in order to target a wide audience. Having no specific information about the victim, they try to make the message body suitable for any possible case.
The key threat here is to send the said compromising materials to all the contacts in the phone book, in all the ways possible. Well, there’s nothing impossible about that, but all these compromising materials are nowadays too easy to refute by saying it is an AI-generated fake. Sure, it is still less than pleasant that you have to make excuses to all of your friends and colleagues, but that’s not even close to a doomsday promised by the “hacker”.
Above I’ve mentioned that the scammer who sends the message may occasionally add a password that the victim really used with one of the accounts. This has an exceptionally frightening effect, making the letter look genuine in the eyes of the user. However, there’s no reason to panic.
You see, it is not hard to get someone’s old password. Credential leaks happen pretty often, usually after a company, website or organization is hacked. Huge dumps of collected credentials are then sold on the Darknet, with free test samples having hundreds of entries. If the fraudulent actor is serious about the scam, they may get hold of a paid database that will cover many more potential victims.
If you read the news about the latest hacks, or just follow the basic cybersecurity rules and change your passwords once every 2-3 months, then these leaks pose no threat to you. By the time all the data is aggregated, sold, and the con actor sends a scam email, that leaked password gets irrelevant.
As this part is a culmination of a scam, there is not a lot going on, and thus it is hard for a scammer to make a mistake. They demand paying anywhere from $1000 to $1500 to prevent the leak of all the aforementioned explicit content, specifying a Bitcoin address as a payment method. Also, there is typically a deadline of 48 hours, which counts from the moment when the email is opened. Obviously, for such a use case, they register a disposable BTC wallet, so the law enforcement won’t have a persistent clue.
Typically for any scam, frauds ensure you against any off-the-road steps, like contacting the police, resetting devices or reaching them back. While the latter two being more or less understandable, the first one is yet another sign of a “Have you heard of Pegasus” scam. The “hacker” tries to cut any connections to the scam as soon as the victim receives the message. No payment confirmation, no afterword – just vanish. If they’re so confident about their anonymity, why can’t they contact them to confirm that the deal is done? One more point of uncertainty here.
The key to how this scam works is social engineering. The number of technical mistakes and logic inconsistency works because of folks’ lack of knowledge on how malware works. Nevertheless, the points to push on are picked rather professionally. Here are the methods of social engineering that fraudsters use in “Have you heard of Pegasus” scam.
One of the biggest fears of any human being is that their secrets will be revealed. Regardless whether it is about which plushie they prefer to sleep with or what category of adult videos they prefer, this always infuses a feel of insecurity or even vulnerability. This, in turn, makes the victim obedient to any of the further instructions, ransom payment in particular.
One more step in making the victim believe what’s said in the email is real is the appeals to a worldwide-known spyware. Pegasus got rather ill fame amongst people, despite being rarely used and inaccessible to black hat hackers. The latter two facts, nonetheless, are not really known to a wide audience, hence the “I’m using Pegasus” trope appears true.
The key thing that the hacker does is threats of public humiliation – a possibility that, in fact, makes the privacy compromise such a scary occasion. This eventually pushes the victim to an obvious step – paying the ransom. That’s exactly what the scammer wants, and a scared person is haste to obey.
Even though the described email is a complete scam, there’s still a possibility that something is present in the system. Not something related to the scammer, but possibly a thing that has leaked your password before. For that reason, I recommend scanning the system with GridinSoft Anti-Malware. Its multi-component detection system will find and remove any malicious programs present on the computer.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

I write about how to make your Internet browsing comfortable and safe. The modern digital world is worth being a part of, and I want to show you how to do it properly.
Absolutely agree! Pegasus is typically used to target high-profile individuals, and unlike regular spyware, it doesn’t require you to click any link to become infected. It’s also extremely expensive and not your average spyware.
To provide the best experiences, we use technologies like cookies to store and/or access device information. Consenting to these technologies will allow us to process data such as browsing behavior or unique IDs on this site. Not consenting or withdrawing consent, may adversely affect certain features and functions.
Functional Functional Always activeThe technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network.
Preferences PreferencesThe technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user.
Statistics StatisticsThe technical storage or access that is used exclusively for statistical purposes. The technical storage or access that is used exclusively for anonymous statistical purposes. Without a subpoena, voluntary compliance on the part of your Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you.
Marketing MarketingThe technical storage or access is required to create user profiles to send advertising, or to track the user on a website or across several websites for similar marketing purposes.